- Office Hour : 09:30 am - 6:30 pm
Stay Informed and Stay Protected
Cyber Security Training Program
Become a cyber security expert with our comprehensive training program. Learn about current threats, best practices for prevention, and incident response. Join now and stay ahead of evolving cyber threats.
4.95 Average Rating
(2000+) Reviews
Training Available 24*7 Call at +91 9513805401

Powerhouse of Expert Trainers
We boasts a vast pool of highly skilled cybersecurity trainers, each bringing extensive hands-on experience in ethical hacking, penetration testing, digital forensics, and network security. With industry-certified professionals and cutting-edge training methodologies, Craw equips individuals and organizations with the latest cybersecurity knowledge and practical skills to combat modern cyber threats. Whether for beginners or advanced professionals, our expert trainers ensure comprehensive learning, real-world applications, and career-ready expertise in the ever-evolving cybersecurity landscape.
Request A Free Demo
Training Available 24*7 Call at +91 9513805401
Best Cyber Security Winter Training Program in Delhi 2025
Get Job Assistance with cyber security training courses
Request A Free Demo
Training Available 24*7 Call at +91 9513805401
Cyber Security Trainings & Certifications
Our Training and Certifications in DelhiOur magnificent and world-class training institutions of Bytecode Cyber Security provides Online training sessions in pre recorded videos, and VILT formats. we are one of the best Cyber Security Training institute. One can also take our interactive live classroom sessions through skilled trainers and mentors.

Cyber Security Trainings & Certifications
Our magnificent and world-class training institutions of Bytecode Cyber Security provides Online training sessions in pre recorded videos, and VILT formats. we are one of the best Cyber Security Training institute. One can also take our interactive live classroom sessions through skilled trainers and mentors.
⇨ Online remote learning
⇨ Expert Trainers
⇨ Lifetime Access
⇨ Course Guidelines
We Offer Professional Cyber Security Certification Courses
We facilitate numerous real-time courses with the pre-set industry standards in the best possible manner through the most experienced and skilled teaching professionals. Moreover, we offer 1 Year and 6 Months Diplomas in Cyber Security Training with the best-in-class latest tools and techniques.
We offer registered and authorized certification from different councils and renowned authorities, to our students from India and to the entire world as an authorized training center for CompTIA, CISCO, Redhat, Python.
Experience
Our great team of more than 1400 software experts.
Quick Support
We’ll help you please call at +91 9513805401
Upcoming Training Batches
Cyber Security Certification Courses
Course Name
Batch Timing
Start date
RH199VT+EX200K
10 am – 12 pm
20 July 2025
RH294VT+EX294K
10 am – 12 pm
20 July 2025
Endpoint Security
10 am – 12 pm
21 July 2025
Ethical Hacking
10 am – 12 pm
20 July 2025
Linux Essentials
3 pm – 6:30 pm
22 July 2025
Penetration Testing
3 pm – 6:30 pm
22 July 2025
Python
3 pm – 6:30 pm
23 July 2025

How to Start a Career in Cyber Security
Contact us : +91 951 380 5401 | 011 – 4039 4315
Top Cyber Security Certifications Training Course
Google Review (1900)
5/5
☉ 6 Months Information Security Diploma Course
☉ 1 Year Cyber Security Master Diploma Course
☉ Ethical Hacking Course Training and Certification
☉ Cyber Forensic Investigation Training and Certification Course
☉ Cisco Certified Network Associate Training and Certification Course
☉ Python Programming Training Course
☉ CompTia Security Plus Training and Certification Course
☉ Cisco Certified Network Professional Training and Certification Course
☉ Red Hat Certified System Administrator Training Course
☉ Mobile Application Security Training Course
☉ Artificial Intelligence Training Course
☉ Python With Data Science Training Course
☉ Machine Learning with data Science Training Course
☉ Web Application Security Training Course
Request A Free Demo
Training Available 24*7 Call at +91 9513805401
Bytecode Cyber Security offers a high level of technical education to the students, clients, and Partners in IT Industry by our Well-Qualified, Certified, and Experienced Trainers.
WHY CHOOSE USClassroom Training
Our world-class trainers will provide you with interactive live projects-based classroom training sessions.
Online Training
One can also choose our online mode of training and study at one’s pace at any favorable time slot and place.
Corporate Training
Our efficient mentors will provide you with an environment so that you can understand and get fit in the real-time jobs in future.
Job Assistance
We provide a “Job Assistance” for the candidates who successfully complete our 1 Year Diploma in Cyber Security Course.
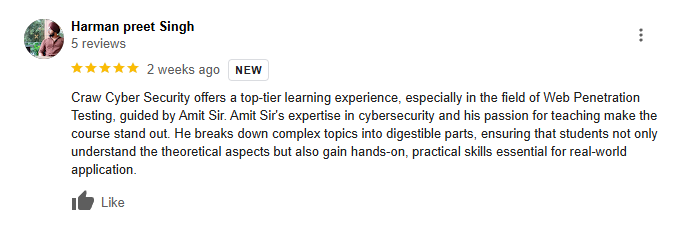
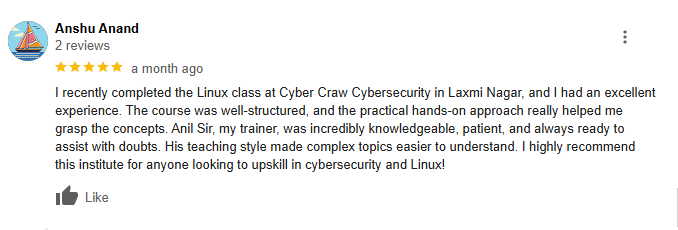
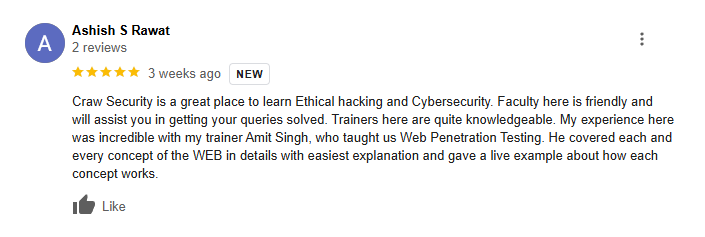
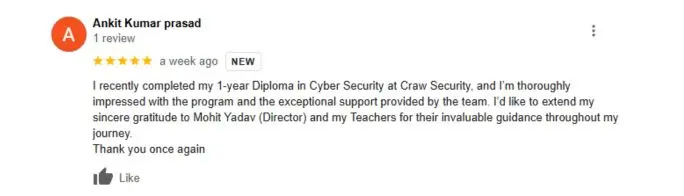
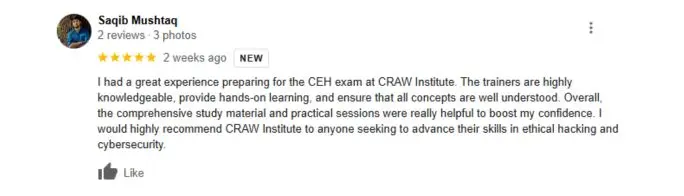
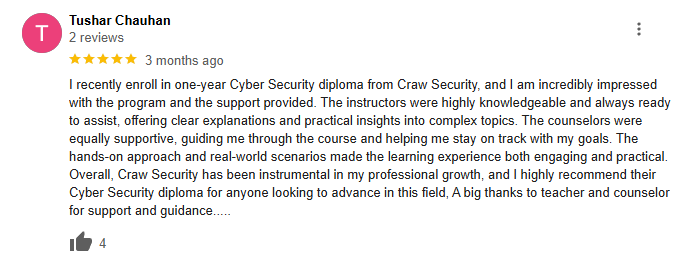
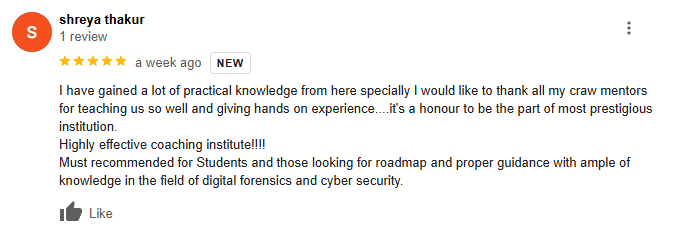
Students Excited With Our Cyber Security Trainings
The magnificent enterprise of Bytecode Security also provides VAPT solutions to numerous IT organizations which want to test the security protocols of their various applications, websites, networking, IoT devices, and other varied interfaces where a potential hacker can compromise. You can contact us for a cost-efficient solution
Request A Free Demo
Training Available 24*7 Call at +91 9513805401
Bytecode Cyber Security Training is India’s leading organization in the field of Information Security Services.
Our VAPT Assessment Services in DelhiThe magnificent enterprise of Bytecode Security also provides VAPT solutions to numerous IT organizations which want to test the security protocols of their various applications, websites, networking, IoT devices, and other varied interfaces where a potential hacker can compromise. You can contact us for a cost-efficient solution for the security of your organization.
best cyber Security Training Institute

Bytecode Classroom Labs
The classroom Environment is one of the most important factors affecting student learning. The students will get a chance to learn from the subject matter experts hailing from several IT organizations in the market.
⇨ Group Discussions
⇨ Weekdays / Weekend Classes
⇨ 24×7 Learner Assistance & Support
⇨ Blended Learning Delivery Model
⇨ Weekly Content Updation
⇨ Live Class Recordings
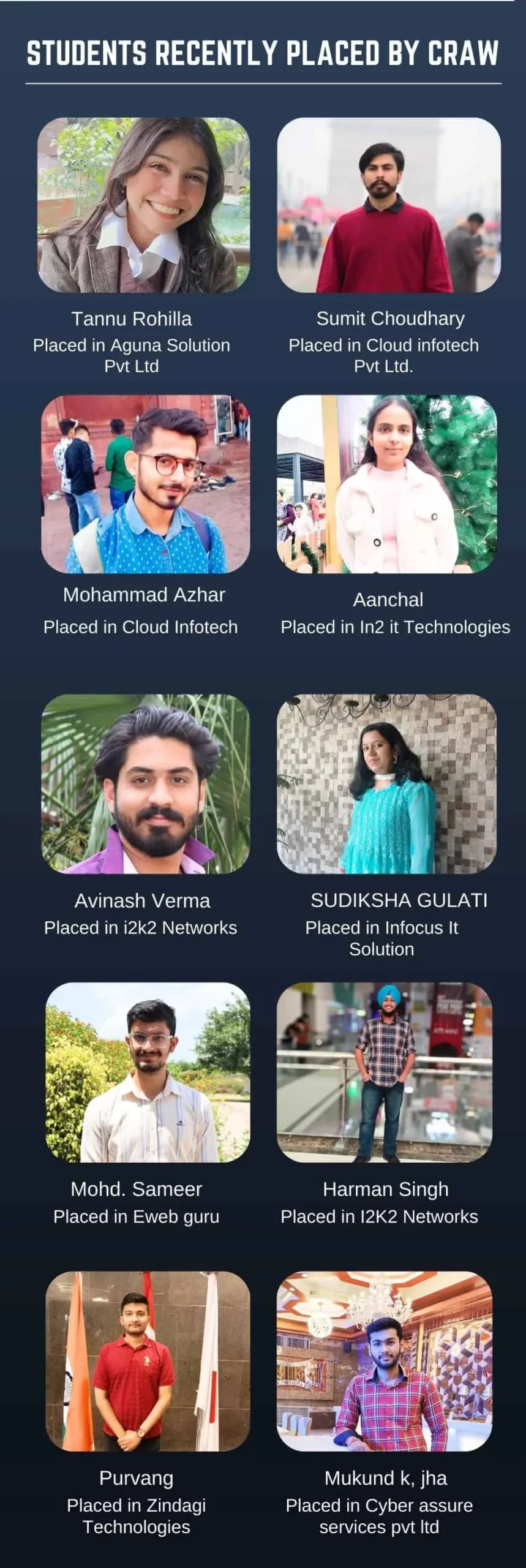
Our Students are placed in Companies













Latest Updates From Bytecode Cyber Security
Connect with Bytecode Cyber SecurityLet Our Students Speak For Us
Testimonial